AWS Identity and Access Management (IAM) is a foundational security service in Amazon Web Services that helps you manage who can access your cloud resources and what actions they can perform. Whether you're spinning up EC2 instances, accessing S3 buckets, or deploying serverless applications, IAM ensures that the right individuals and services have the right level of access.
With IAM, you can securely control access to AWS services and resources for your users. You can create and manage AWS users and groups, use permissions to allow or deny their access to AWS resources, and enable temporary access through roles. IAM is available at no additional cost and plays a crucial role in maintaining a secure and well-governed cloud environment.
What are IAM Identities?
IAM identities are the core elements within AWS IAM that define "who" can access your resources and what level of access they are granted. IAM identities are associated with users, groups, or roles, each with specific permissions that determine which AWS resources they can interact with.
IAM identities can be broken down into several components:
- IAM Users: Individual entities representing a person or application that needs to access AWS resources. An IAM user is typically assigned a unique set of credentials, such as a username and password or access keys, which can be used to sign in to the AWS Management Console or make programmatic API requests.
- IAM Groups: A collection of IAM users. Groups make it easier to manage permissions by grouping users with similar access needs. Instead of assigning permissions to individual users, you assign them to a group, and all members of the group inherit those permissions.
- IAM Roles: Roles are similar to users, but they are meant to be assumed by entities such as AWS services (like EC2 or Lambda) or IAM users for temporary access to resources. Roles are often used for automated processes or cross-account access where the permissions are needed for a short duration or specific tasks.
- Root User: The initial user created when an AWS account is set up. The root user has unrestricted access to all resources and services in the AWS account, and it is generally recommended to avoid using the root user for everyday tasks. Instead, IAM users and roles should be used to control permissions.
The IAM identities (users, groups, and roles) interact with IAM policies to define what actions those identities can perform on specific AWS resources.
What are IAM Policies?
IAM policies are documents that define permissions granted to IAM identities (users, groups, and roles). Policies are written in JSON (JavaScript Object Notation) format and specify what actions are allowed or denied on specific AWS resources.
Policies consist of several key components:
- Effect: Specifies whether the policy allows or denies access. The value can be "Allow" or "Deny".
- Action: Defines the specific actions (such as s3:ListBucket or ec2:StartInstances) that are allowed or denied for a given resource.
- Resource: Defines which AWS resources the policy applies to, using Amazon Resource Names (ARNs) to uniquely identify them.
There are two primary types of IAM policies:
- Managed Policies: These are predefined policies that can be AWS-managed or customer-managed. AWS-managed policies are created by AWS to serve common use cases (e.g., AmazonS3FullAccess), while customer-managed policies are created by you to fit the specific needs of your organization.
- Inline Policies: These are policies embedded directly within IAM identities (users, groups, or roles) and are typically used for very specific, non-reusable permissions. Inline policies provide a fine-grained control over permissions but can be harder to manage as your IAM setup grows.
By attaching policies to IAM identities, you define what actions those identities can perform on which resources. This is the core mechanism of managing permissions in AWS.
How AWS IAM Works?
AWS IAM works on the principles of authentication and authorization:
- Authentication is about verifying who is making the request—be it a user, role, or application.
- Authorization defines what that entity is allowed to do.
When a request is made to access an AWS resource, IAM checks the attached policies to determine if the request should be allowed or denied. These policies use elements like:
- Actions (e.g., s3:GetObject)
- Resources (identified using ARNs – Amazon Resource Names)
- Effect (Allow or Deny)
IAM always denies access by default. Only explicitly allowed actions in policies are permitted. In cases where there's a conflicting “Allow” and “Deny,” the explicit deny always wins.
IAM also enables fine-grained access control by letting you specify who (users, groups, roles) can access which resources, and how they can interact with them.
IAM Features
AWS Identity and Access Management (IAM) offers a suite of features that provide secure and flexible access control to your AWS resources. These features help ensure that only authorized users, workloads, and services have access to the right resources.
Below are the most important IAM features that organizations rely on for secure and efficient cloud management:
- Fine-Grained Access Control
Fine-grained access control is one of the core functionalities of IAM. Using IAM policies, you can precisely specify which AWS services and resources users or workloads can access and under which conditions. These policies let you define:
- Specific actions: Granting access to particular APIs or services.
- Resources: Determining which resources (e.g., EC2 instances, S3 buckets) users can interact with.
- Conditions: Setting conditions such as access only from certain IP addresses or AWS organizations.
This approach ensures you can enforce the least privilege principle, giving users and applications only the access they need to perform their tasks.
- IAM Roles
IAM roles allow delegation of access to AWS services, users, and applications, ensuring temporary access based on specific needs. Roles are a security best practice because they provide:
- Temporary security credentials: When users or services assume a role, they receive short-lived credentials that don’t need to be managed or rotated.
- Delegated access: Users or services can assume roles to perform specific tasks without permanent permissions.
For example, when federating workforce identities into AWS using IAM Identity Center, roles are assigned to control what level of access users will have when they authenticate with their corporate credentials.
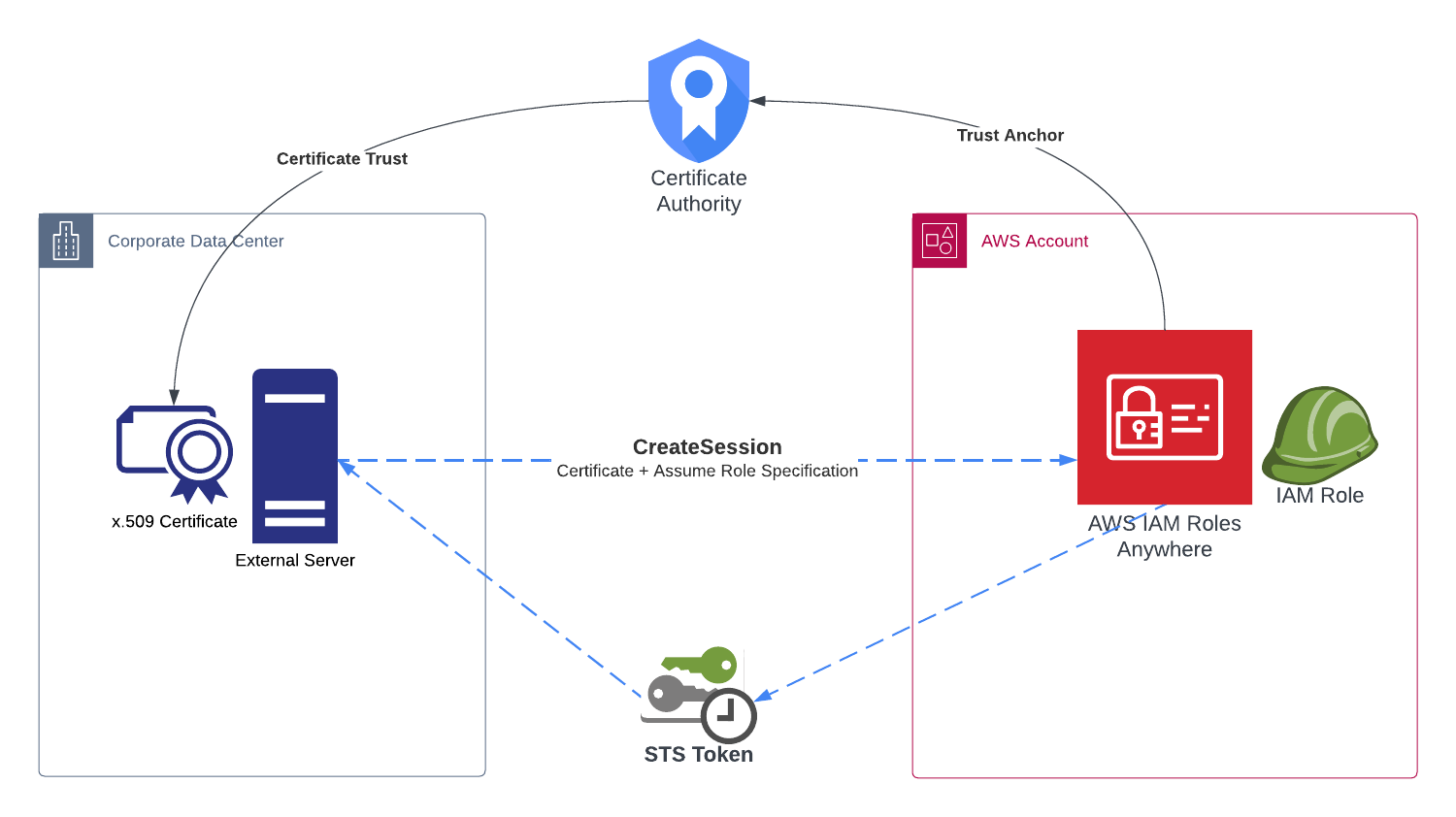
IAM Roles Anywhere
IAM Roles Anywhere extends IAM roles to workloads running outside of AWS, such as on-premises or in hybrid and multicloud environments. It allows these workloads to obtain temporary AWS credentials and use IAM roles and policies for accessing AWS resources securely. This feature is essential for organizations with complex infrastructures that need to manage resources across different platforms while maintaining consistent security policies.
- IAM Access Analyzer
IAM Access Analyzer helps organizations ensure they’re following the principle of least privilege by continuously analyzing and refining IAM policies. It allows you to:
- Identify over-permissioned access: Review IAM roles and policies to uncover any unnecessary or overly permissive access.
- Set, verify, and refine permissions: Streamline the permissions management process as access requirements evolve.
Access Analyzer gives you detailed visibility into the permissions granted within your AWS environment, making it easier to manage and improve your security posture over time.
- Multi-Factor Authentication (MFA)
To further enhance security, AWS supports Multi-Factor Authentication (MFA) for IAM users and roles. MFA adds an extra layer of protection by requiring users to authenticate using something they know (a password) and something they have (an MFA device). Enabling MFA reduces the risk of unauthorized access even if a user's credentials are compromised. - Permissions Guardrails
Using service control policies (SCPs) in AWS Organizations, you can set permissions guardrails across your organization. SCPs enable centralized control over what IAM roles and users can access within the organization's accounts, allowing you to:
- Define maximum allowed permissions for all accounts within the organization.
- Restrict access to critical resources and services to reduce risk.
This centralized approach to access management simplifies the enforcement of security policies across multiple accounts and helps ensure that access boundaries are respected at all levels.
- Attribute-Based Access Control (ABAC)
ABAC allows you to create fine-grained permissions based on attributes attached to IAM roles, such as department, job title, or team name. ABAC enables dynamic and scalable access control, especially in organizations with large and diverse user bases. By linking permissions to specific attributes, you can simplify the creation of policies, avoiding the need to manually update permissions for each resource. - Manage Root Access
With AWS Organizations, you can centrally manage root access for all member accounts, allowing for easier administration of highly privileged tasks. This centralized control ensures that you can securely manage root credentials, reducing the risk of unauthorized changes or configurations that might compromise the security of your AWS environment.
These are some of the major IAM features that help streamline security, access control, and governance within your AWS environment. However, IAM offers several more capabilities to support your cloud security needs. To explore additional IAM features, refer to the comprehensive IAM documentation below:
With these IAM features, AWS enables secure, scalable, and highly customizable identity and access management for your cloud infrastructure. Whether you're managing workforce identities, integrating third-party services, or securing multi-cloud environments, IAM provides the flexibility and control needed to protect your AWS resources.
What are some AWS IAM Best Practices?
To maintain a secure and compliant AWS environment, implementing IAM best practices is crucial. Below are key practices to follow:
- Enable Multi-Factor Authentication (MFA)
MFA provides an additional layer of security, ensuring that even if a password is compromised, unauthorized access is prevented. Always enable MFA for the root account and other important users to safeguard sensitive data. - Use IAM Roles Instead of IAM Users
IAM roles provide temporary credentials that automatically rotate, reducing the exposure of long-term credentials. For applications running on EC2 instances, avoid hardcoding access keys and instead, assign IAM roles to EC2 instances to securely access AWS resources. - Follow the Principle of Least Privilege
Grant users and roles only the permissions they need to perform their tasks. Regularly review and update permissions to ensure they remain appropriate. This minimizes the risk of accidental or malicious actions. - Regularly Rotate Access Keys
Access keys should be rotated regularly to avoid unauthorized access. AWS allows you to create two active keys per user, enabling seamless key rotation without downtime. - Use IAM Groups for Permission Management
Instead of assigning permissions to individual users, use IAM groups. Assign permissions to these groups, which simplifies permission management, especially as your organization scales. - Monitor and Audit IAM Activities
Enable AWS CloudTrail to log all IAM-related activities. Regularly review these logs to identify any unusual or unauthorized actions, helping maintain security and compliance. - Apply Strong Password Policies
Enforce strong password policies, requiring a mix of uppercase, lowercase, numbers, and special characters. Additionally, set up regular password changes and prevent users from reusing old passwords. - Limit the Use of the Root Account
The root account has unrestricted access to AWS resources. Use it sparingly and create IAM users for routine tasks, always enabling MFA for the root account.
By following these IAM best practices, you can significantly reduce security risks and ensure your AWS resources remain well-protected.
AWS IAM FAQs
- Q1. How is IAM different from AWS Organizations?
IAM controls access within a single AWS account, while AWS Organizations manages multiple accounts, enabling centralized governance, consolidated billing, and policy enforcement across accounts. - Q2. What’s the difference between IAM users and IAM roles?
IAM users have long-term credentials for individuals. Roles provide temporary credentials for services, applications, or users—ideal for secure, short-term access. - Q3. Can IAM be used for hybrid or on-prem environments?
Yes. IAM Roles Anywhere lets external workloads use X.509 certificates to securely obtain temporary AWS credentials for accessing AWS services. - Q4. What is role-based access control (RBAC)?
RBAC assigns permissions based on job functions. IAM implements RBAC through roles aligned to specific tasks, improving access control and auditability. - Q5. Can IAM be used with third-party identity providers?
Yes. IAM supports SAML 2.0-based identity federation, enabling access for users from corporate directories or other identity providers without creating IAM users. - Q6. What is attribute-based access control (ABAC)?
ABAC grants permissions based on resource and user attributes (tags). It allows fine-grained, scalable access management, especially useful in growing environments. - Q7. How do I remove unused permissions in IAM?
Use “last accessed” data in IAM to identify and remove inactive users, roles, and permissions. This helps maintain least-privilege access. - Q8. What is the IAM policy simulator?
It’s a tool that lets you test and troubleshoot policies by simulating access requests, helping you validate and debug permissions. - Q9. Can IAM restrict access by IP address?
Yes. IAM policies can include conditions that allow or deny access based on specific IP ranges, enhancing access control. - Q10. How many IAM users can I create per account?
You can create up to 5,000 IAM users per AWS account. For scaling beyond that, use IAM roles or identity federation.
Build a Robust IAM Setup for Your AWS Cloud with CloudKeeper
Make sure your IAM framework and user access are securely managed to meet your business needs with CloudKeeper by your side. With our 24x7 Personalized Cloud Support, we provide end-to-end cloud assistance, including the creation and management of IAM roles, architecture optimization, DevOps consulting, third-party tech stack guidance, and cloud cost optimization.
Moreover, our savings platforms like CloudKeeper Auto use basic read-only IAM roles with zero access to your user or business data, delivering substantial cost savings without compromising security. Book a free consultation with one of our experts to know how CloudKeeper can help you optimize your cloud infrastructure.