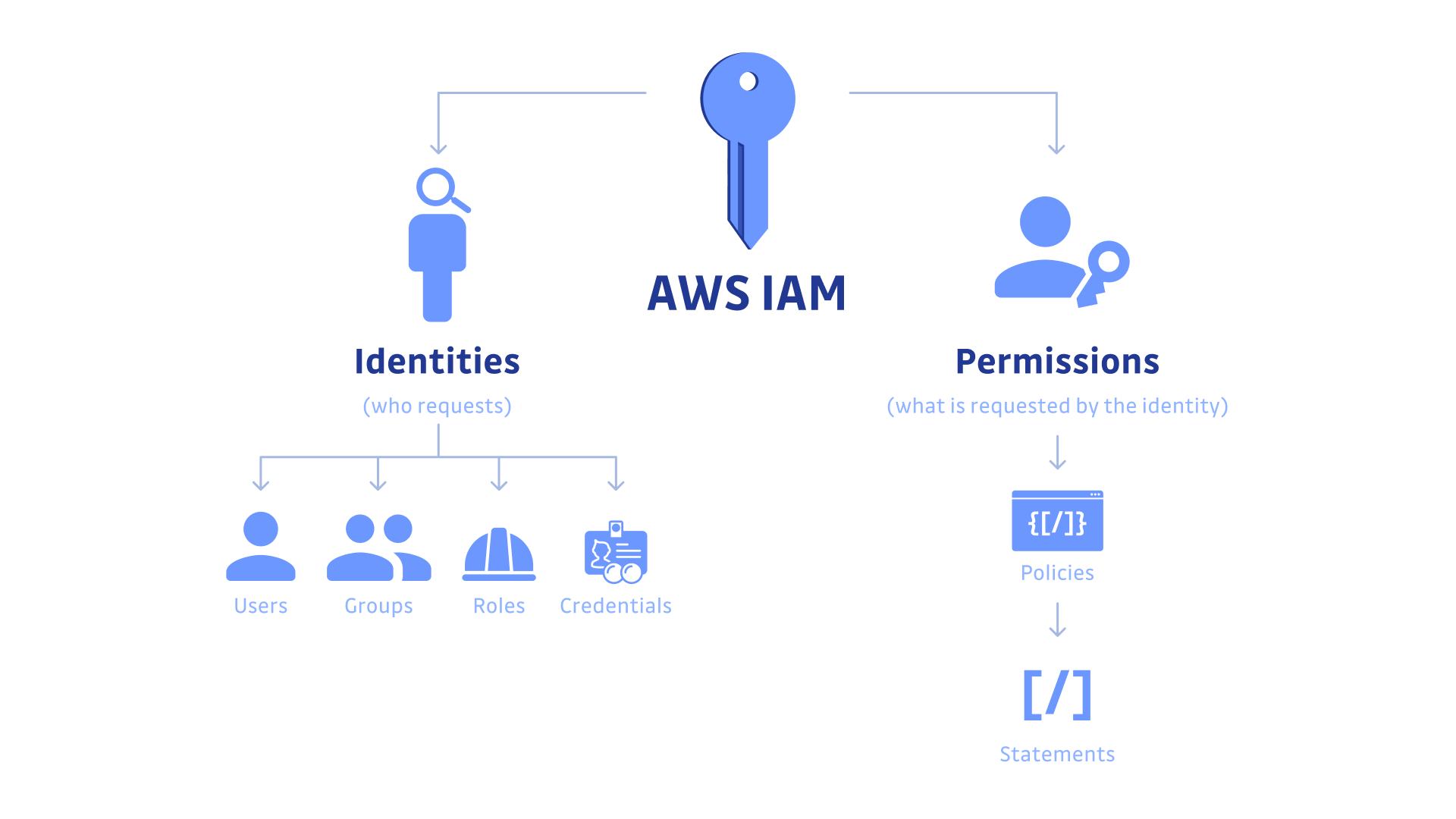
IAM (Identity and Access Management) security best practices refer to a set of guidelines and strategies designed to protect AWS resources by ensuring that only authorized users and applications have the appropriate access. By implementing these practices, organizations can minimize security risks and maintain a robust security posture in the cloud.
WebinarUnlock 31% YoY Growth: 5 Ways to Turn AWS Cost Concerns into Customer Expansion