DevOps Engineer
Simran has a knack for integrating tools and automating workflows to improve efficiency and scalability.
Amazon Managed Grafana (AMG) provides a secure, scalable way to visualize and analyze data from multiple sources. One of the key requirements in enterprise environments is integrating Grafana with existing identity providers for Single Sign-On (SSO).
In this post, we’ll configure Amazon Managed Grafana to use Google Workspace as an Identity Provider via SAML 2.0 so your users can log into Grafana with their Google credentials.
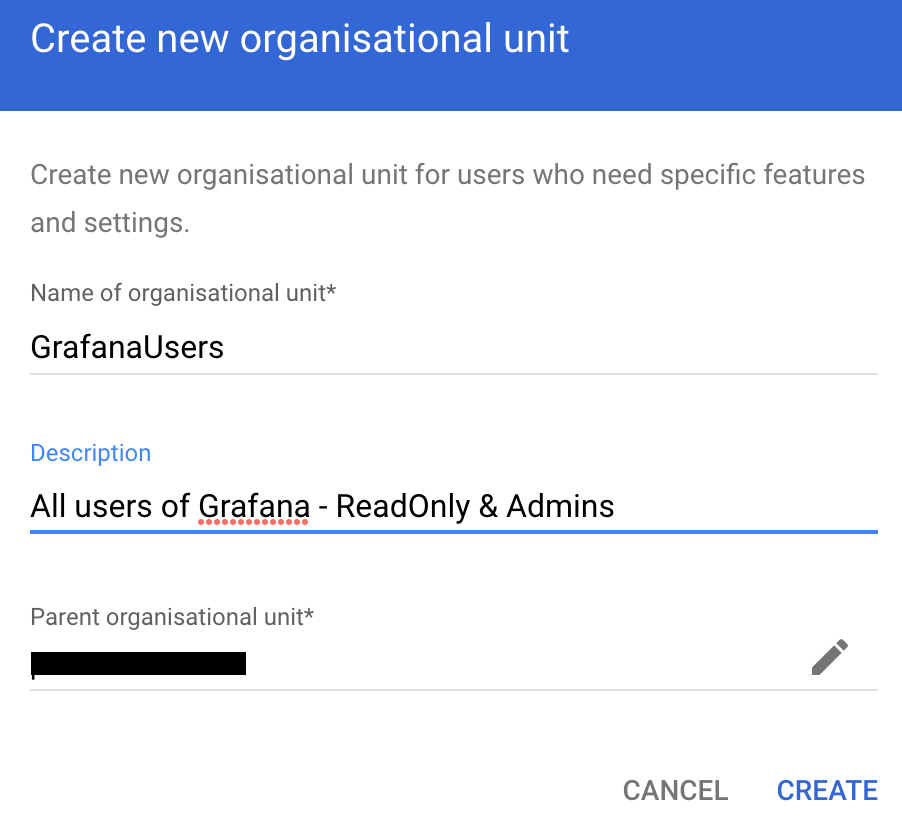
1. Create an Organizational Unit (OU) in Google Workspace (e.g., GrafanaUsers) and place intended Grafana users in it. By default, they’ll have read-only access.
2. Decide who should be Grafana admins and, for each, set User Information → Employee Information → Department = Grafana in the Google Admin Console.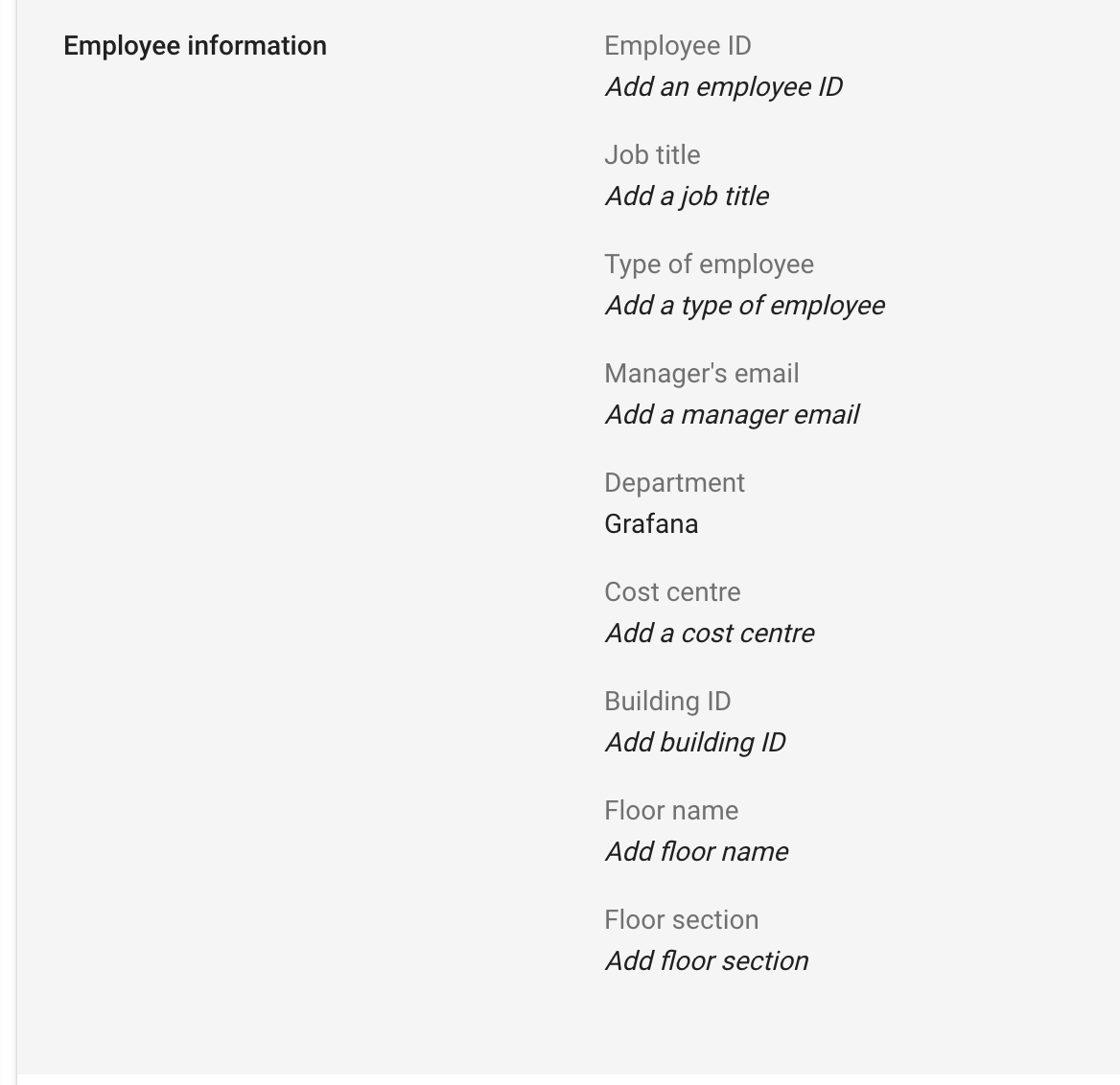
You can also use a custom field or any available field here, but note that it has to be updated in Step 3 too.
3. (Optional) Create environment-specific groupings if you run multiple workspaces (dev/stage/prod).
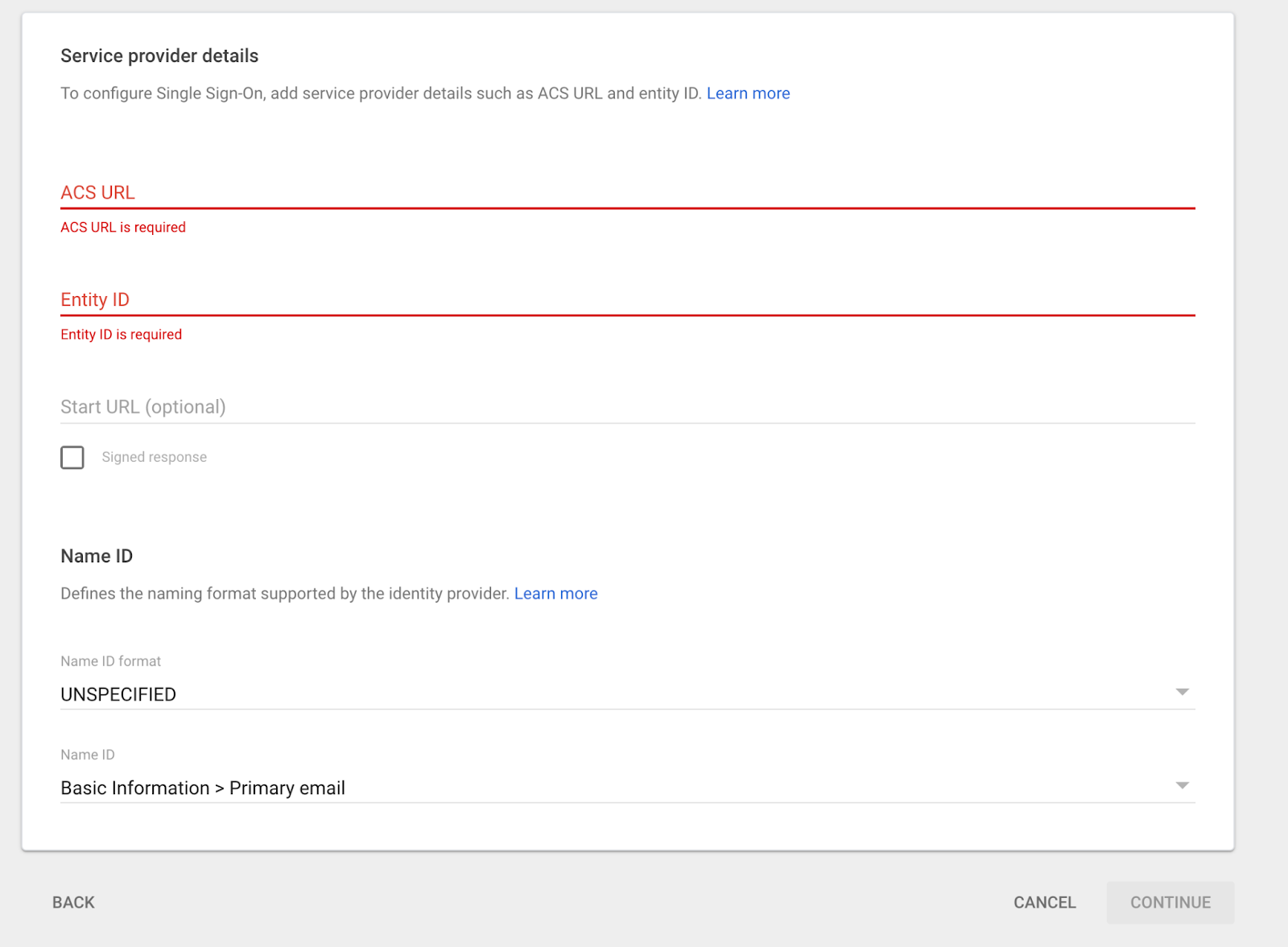
In Google Admin Console → Apps → Add custom SAML app, create a new app (e.g., Amazon Managed Grafana Prod) and download the IdP metadata file.
When asked for the service provider details, take a pause and move on to Step 2 of this blog.
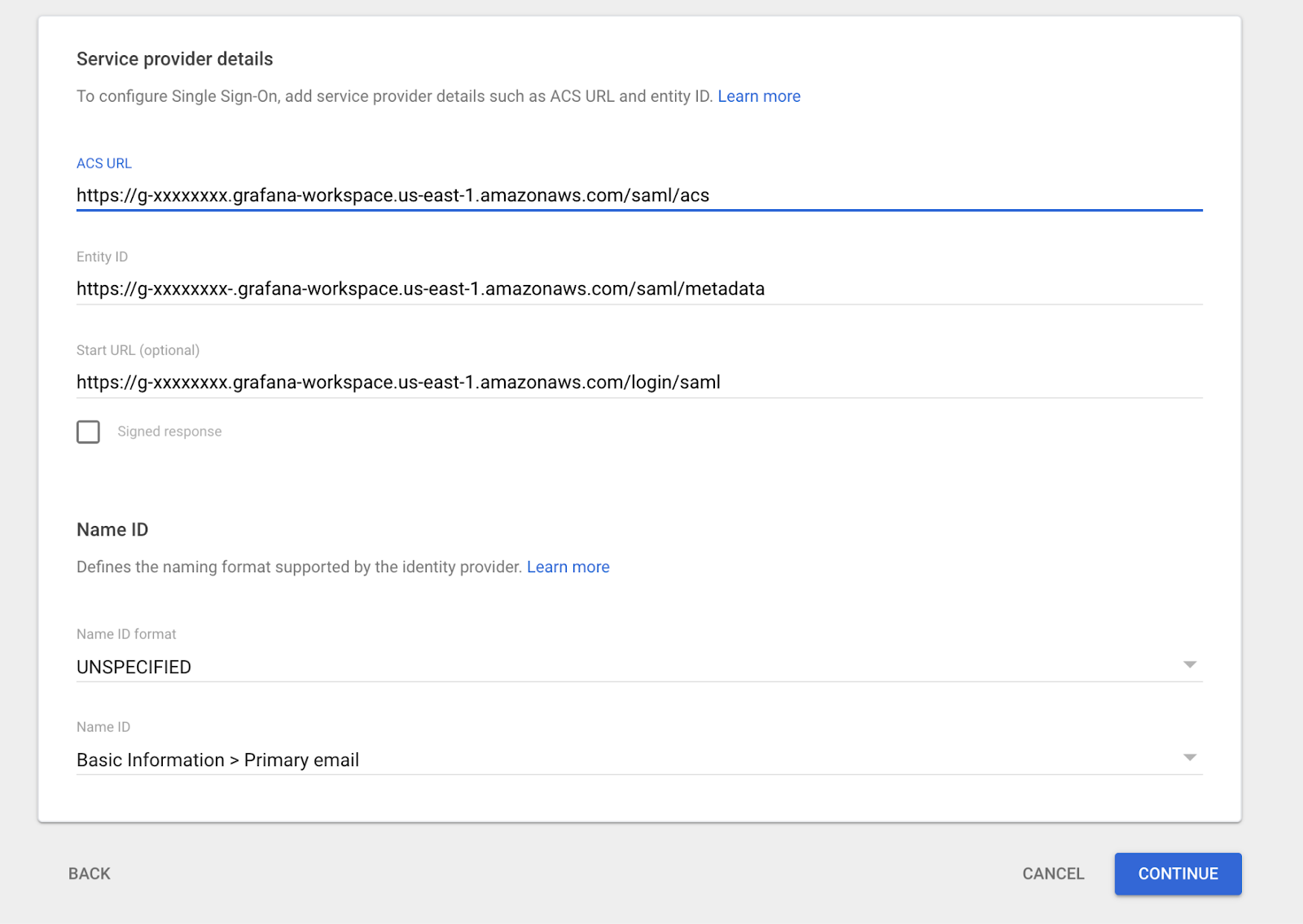
Open Amazon Managed Grafana → your workspace → Authentication → Security Assertion Markup Language (SAML) → Complete Setup. Copy the values AWS shows for:
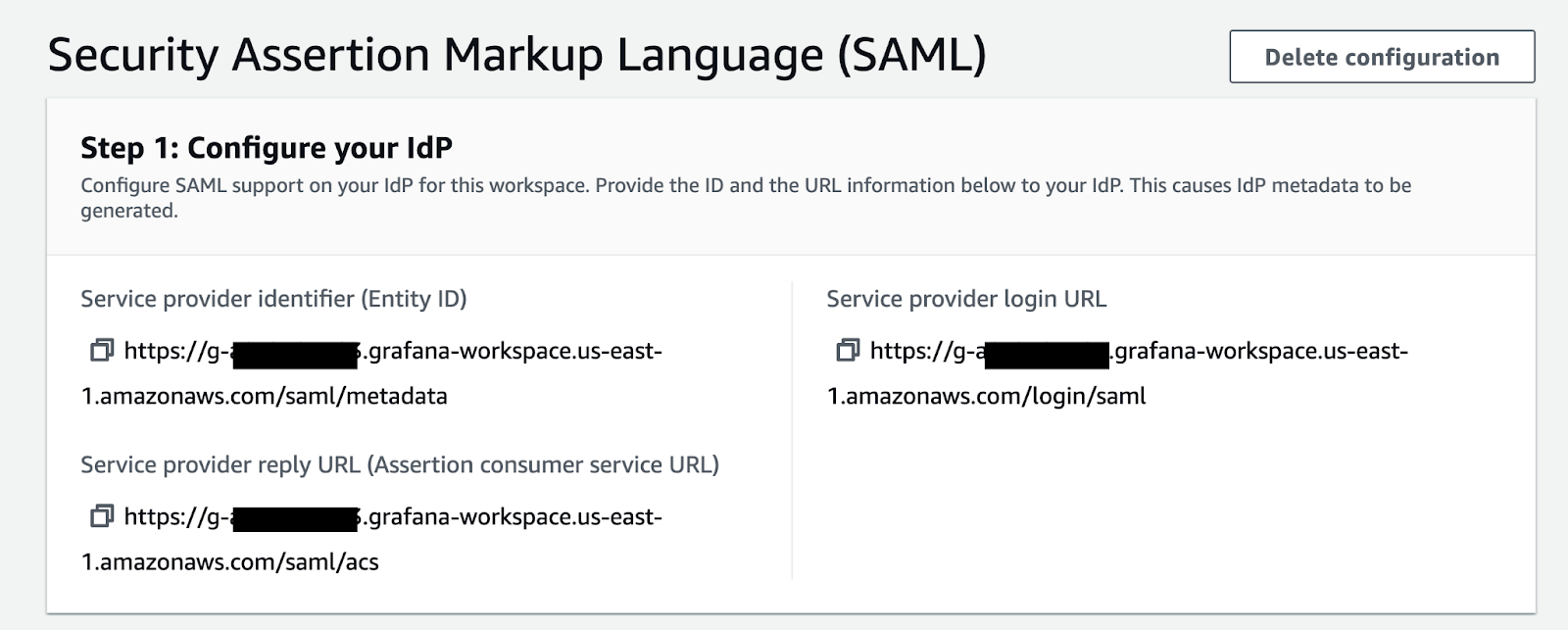
Put these values in the Google Workspace page where you were setting up the SAML app.
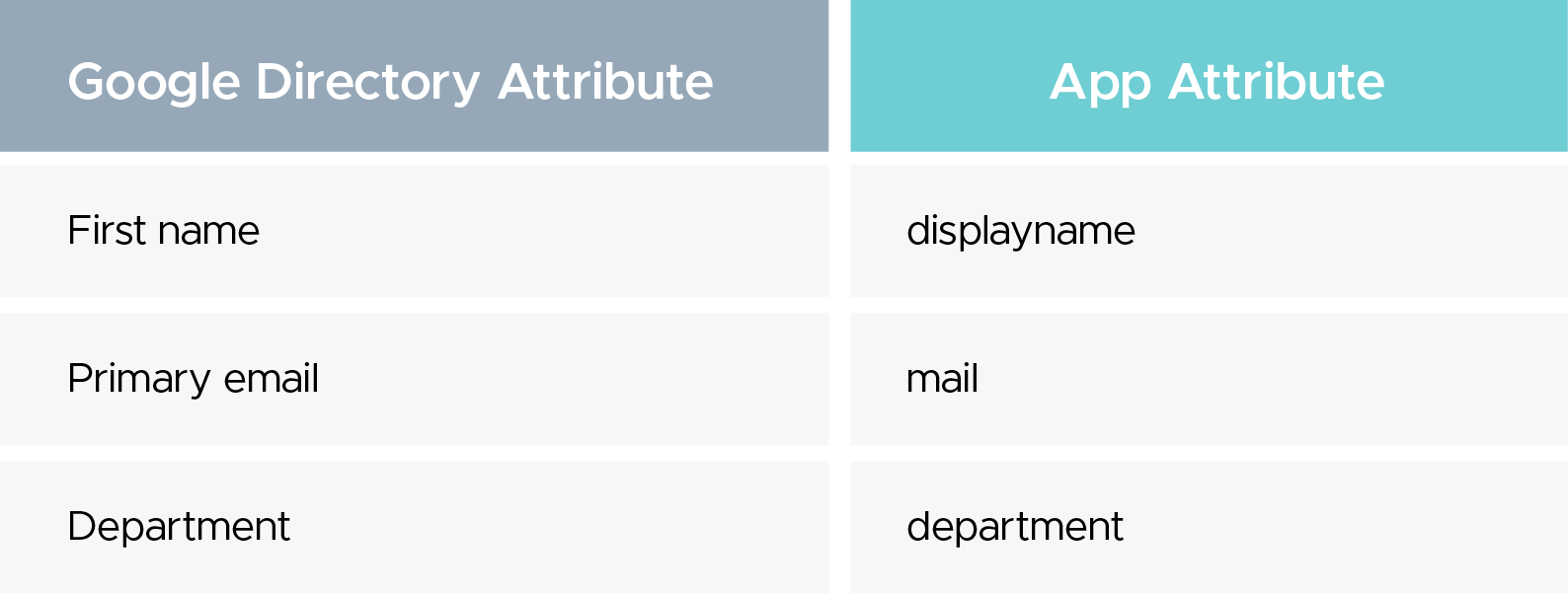
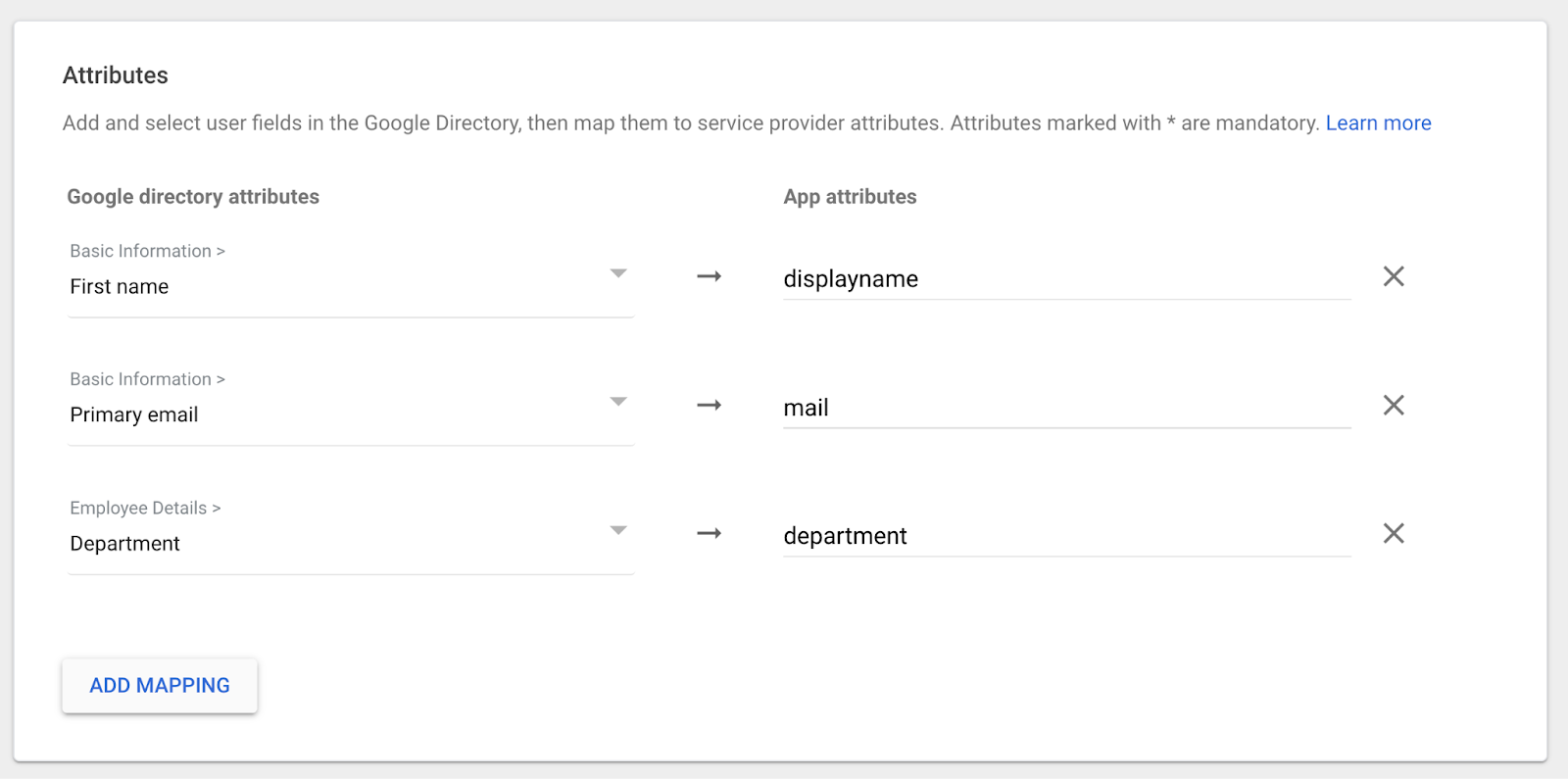
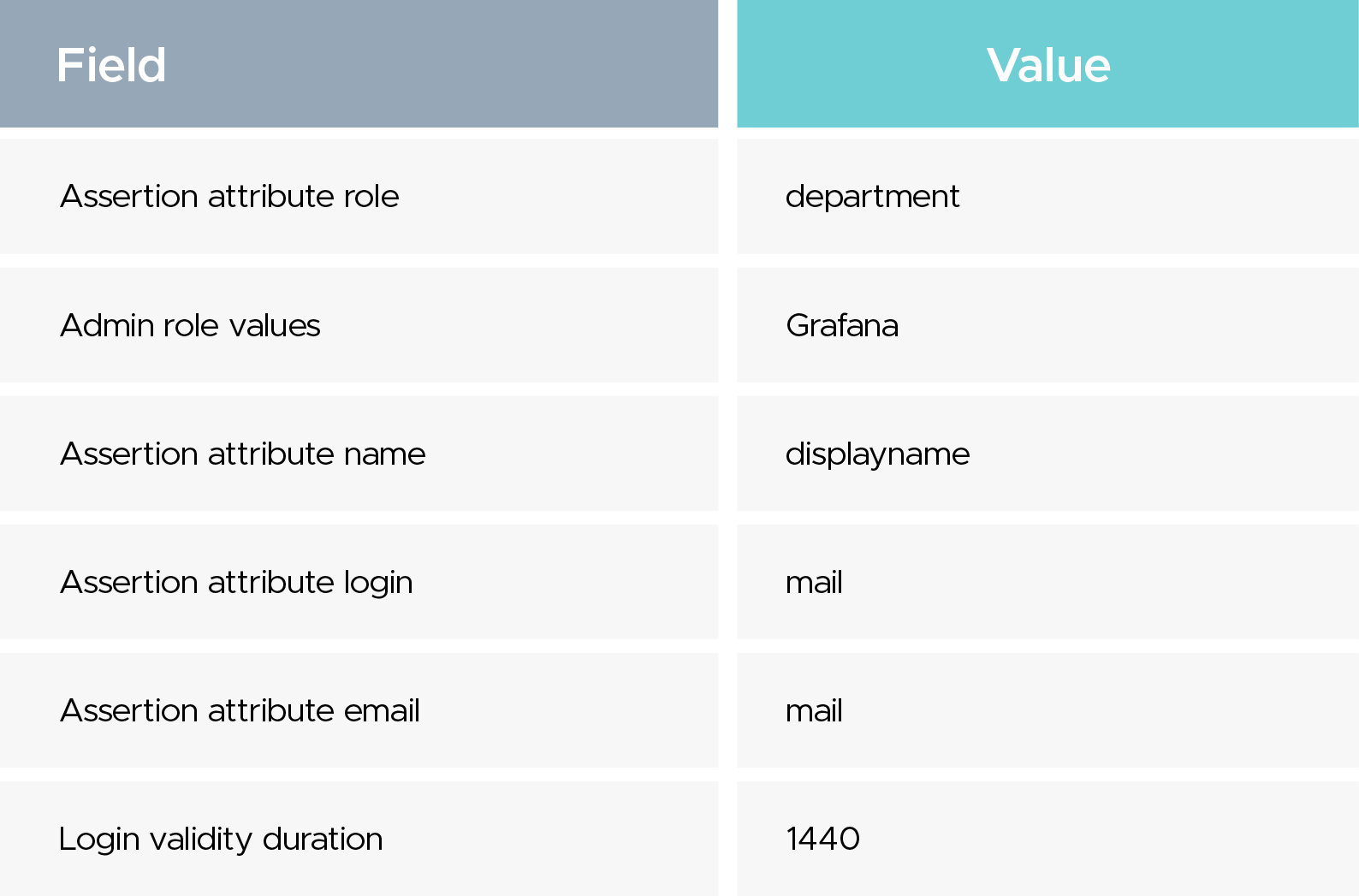
In your Google Workspace SAML app, add these mappings so Grafana can assign identities and roles correctly:
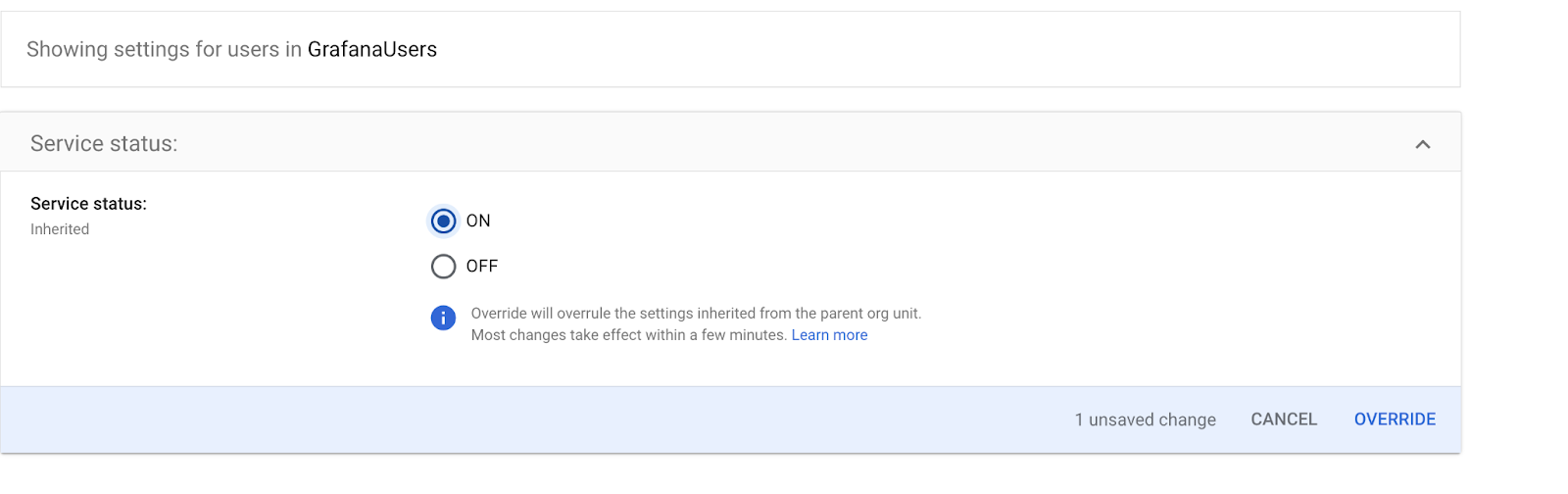
In the Google Workspace SAML app User Access, target the GrafanaUsers OU and set Service status = On, then hit the Override button.
Upload the IdP metadata you downloaded from Google Workspace and complete the following fields:
Visit your Grafana URL and click Sign in with SAML. You’ll be redirected to Google to pick/confirm the permitted account and then returned to Grafana.

If you see “app not enabled for user”, verify:
With this configuration, your organization centralizes authentication for Amazon Managed Grafana using Google Workspace. It simplifies onboarding, keeps roles consistent, and leverages your existing identity controls.
Questions or need assistance? Contact CloudKeeper for personalized support and ensure your cloud infrastructure setup runs smoothly.
Speak with our advisors to learn how you can take control of your Cloud Cost