Problem Statement
When building sandbox or proof-of-concept (POC) labs in AWS, isolation and governance quickly become necessary.
Creating a handful of accounts manually in the AWS Management Console is manageable, but provisioning 20, 50, or 200 accounts is tedious, error-prone, and inefficient.
Challenges include:
- Automating account creation at scale
- Managing access dynamically for users
- Keeping costs under control while ensuring security and compliance
Solution Overview
By combining AWS Control Tower for governance with Account Factory for Terraform (AFT) for automation, you can:
- Deploy a multi-account landing zone with centralized governance
- Automate the provisioning of hundreds of sandbox/demo accounts
- Manage user access flexibly using AWS IAM Identity Center
- Automate cost cleanup using AWS Nuke
Architecture Overview
1.Control Tower Landing Zone
- Audit Account → for compliance checks (restricted, no direct login).
- Log Archive Account → centralized logs (CloudTrail, AWS Config).
- Sandbox OU → dedicated for lab/demo accounts.
2.Account Provisioning
- Small scale: Account Factory console.
- Large scale: AFT with Terraform definitions.
3.Access Management
- Group-based access: one group with AdminAccess across all accounts.
- Dynamic assignment: allocate sandbox accounts to users on-demand.
4.Cost Management
- Cleanup automation with AWS Nuke on a scheduled basis.
Scalable Automation with AFT
Instead of creating accounts manually:
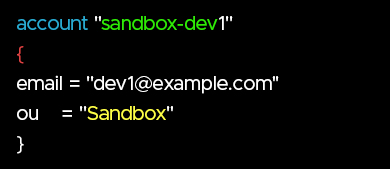
- Define accounts as Terraform resources.
- Generate requests from a CSV or database if provisioning hundreds of accounts.
- Unlike console-based creation, AFT does not require assigning users at creation.
- You can build an account pool first and assign users later using the create-account-assignment API.
Automated Cleanup with AWS Nuke
Creating 200 sandbox accounts means there’s always a risk of resource sprawl and rising costs. The solution is to use AWS Nuke for periodic cleanup.
How It Works
- EventBridge Rule → Triggers cleanup (nightly or weekly).
- Lambda Function → Spins up an EC2 instance.
- EC2 Instance → Assumes IAM role in child account.
- AWS Nuke → Deletes all resources in the child account.
AWS Nuke Configuration Example
A minimal nuke-config.yml:
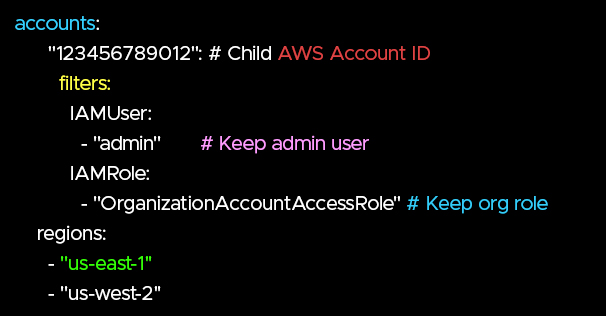
Considerations for Cleanup
- Always test in non-production accounts first.
- Exclude mandatory roles like OrganizationAccountAccessRole.
- Run on a schedule that balances cost savings with availability for labs (e.g., nightly, weekly, or monthly).
- Monitor via CloudWatch metrics and alarms for failed cleanup runs.
- Keep the cleanup automation in the management account for central control.
Cost Considerations
- Centralize logs in the log archive account to avoid duplication.
- Use shorter retention periods for CloudWatch logs and export to S3 if needed.
- Enforce cleanup schedules with AWS Nuke to minimize idle costs.
- Apply guardrails with Control Tower to enforce security/compliance automatically.
Results
With this setup, you achieve a governed, scalable, and cost-efficient lab environment:
- Isolated accounts for users or groups
- Automated provisioning with Terraform (AFT)
- Flexible access management with Identity Center
- Automated cleanup and cost control with AWS Nuke
This provides the agility of quick sandbox environments while maintaining control and keeping costs predictable.

